-
Suggestion
-
Resolution: Unresolved
-
579
-
-
As per the user-provisioning documentation the feature currently supports the sync of:
- Display name
- Email address
- Organization
- Job title
- Timezone
- Department
- Preferred language
From provisioning perspective, it would be a good feature to allow custom attributes from third party IDPs to be synced into the Atlassian accounts. Sample use cases:
- Profile photos
- Location/Office/Based in
- Manager (JSD approvals automatically set to the user's Manager)
- Employee ID
- Student ID's
- Cost center
- is duplicated by
-
ACCESS-766 Based in (location) cannot be updated via user provisioning
-
- Closed
-
-
ACCESS-785 Support Syncing User's Profile Photo with SCIM User Provisioning
- Closed
-
ACCESS-883 Allow to sync profile photos from external identity providers
- Closed
-
ACCESS-886 Include profile picture in azure user provisioning
- Closed
-
ACCESS-1417 Sync additional information to Atlassian Account using GSuite
- Closed
-
ACCESS-1626 Allow for the ability to take profile information from external sources
- Closed
-
CLOUD-11126 Allow Customized Attribute Mapping from Identity Provider
- Closed
-
ID-7724 Active Directory profile picture sync
- Closed
-
ACCESS-657 Support more attributes for user-provisioning
- Closed
-
ACCESS-1487 Push Other Attributes from an IDP to Atlassian Cloud Managed Profiles
- Gathering Interest
- relates to
-
ACCESS-1240 Sync Atlassian teams from identity provider via SCIM
- Closed
-
ACE-5271 Loading...
-
ACE-5310 Loading...
- blocks
-
LINK-4558 Loading...
- is addressed by
-
ENT-406 Loading...
- links to
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
All comments
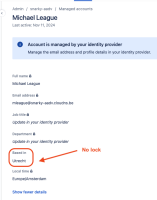

How about being able to provision in a user's phone number? I would think this is pretty basic