-
Type:
Suggestion
-
Resolution: Done
-
3,082
-
108
Hello all,
Quick update to let you know we've release JSM external customer (Portal-only account) SSO for everyone.
We have completed rollout to all sites
Cheers,
Ash.
Problem Definition
Currently it is not possible to integrate sso with JIRA Service Desk, it would be better if can provide this functionality so that customer does not need to sign in to the customer service portal in order to raise a request.
Workaround
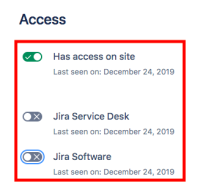
If the customer (portal-only user) has an email address verified with Atlassian Access, site-admin can migrate the account to Atlassian account so that the customer can login with SSO.
Once migrated, ensure that the site access is enabled and ensure that there is no application access. This will ensure that there are no license consumed and have the users treated as a customer.
- duplicates
-
JSDCLOUD-1015 Active Directory integration for customers
- Closed
- is blocked by
-
JSDCLOUD-1244 Create a Crowd SSO authenticator that will allow Customers to be authenticated from the local directory
- Reviewing
- is duplicated by
-
JSDCLOUD-1049 Authenticate Customers via Ldap
- Closed
-
JSDCLOUD-8372 SSO option at the JSD Portal
- Closed
- is related to
-
JSDCLOUD-1498 JIRA Service Desk Authentication Documentation
- Closed
-
JSDCLOUD-8135 Create a public REST endpoint for resetting Jira Service Desk customer account passwords
- Closed
-
JSDCLOUD-8239 Customer accounts: Support SSO via other methods and identity providers(IdP) e.g. SSO via JWT
- Closed
-
JSDSERVER-630 SSO integration with Jira Service Desk
- Closed
-
ENT-171 Loading...
-
ENT-1538 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...