-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Low
-
Affects Version/s: 5.4.20, 5.12.22, 10.3.5, 10.5.1
-
Component/s: Request Type Configuration
-
1
-
Severity 3 - Minor
Issue Summary
As described on Setting up request types, JSM DC allows project administrators to specify hidden fields with preset values. This includes the "Security Level" system field, which defines an issue security level. The level specified here will override the scheme's default during issue creation.
If an administrator migrates the project to a new issue security scheme, this preset value is not updated and will continue to apply the old security level. When new customer requests are created, they can't be viewed in the UI, even by users granted access. Other fields will produce a clear warning in both the Jira UI and the customer portal.
The root cause of this behavior is JRASERVER-67812. It causes other related bugs, such as JRASERVER-74605.
Steps to Reproduce
- Create a service project and issue security scheme with at least one security level.
- Associate that project with the issue security scheme.
- Add the "Security Level" system field to the project's "create issue" screen.
- Add a new request type and make "Security Level" a hidden field, with the security level as the default value.
- Create a second issue security scheme.
- Migrate the project to the second issue security scheme.
- Create a new customer request.
Expected Results
The customer portal presents an error when a user submits a request. Project administrators are provided a warning in the Jira UI. This is the behavior with other fields.



Actual Results
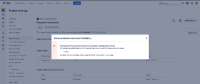
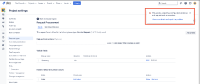
The customer portal allows the request to be submitted without warning:

Neither the customer nor any agent can view it from the portal or Jira UI:


Workaround
Prevent corruption of new issues
Edit the present value from the request type to ensure it uses an applicable security level. You can accomplish this by showing and re-hiding the "Security Level" field from the field editor under request types.
![]() You can find invalid preset values with this database query:
You can find invalid preset values with this database query:
WITH security_form_fields AS (SELECT p.id AS project_id, p.pkey AS project_key, p.pname AS project_name, portal."ID" AS portal_id, portal."NAME" AS portal_name, form."ID" AS request_type_id, form."NAME" AS request_type_name, fvalue."VALUE" AS issue_security_level FROM project p JOIN "AO_54307E_VIEWPORT" portal ON p.id = portal."PROJECT_ID" JOIN "AO_54307E_VIEWPORTFORM" form ON portal."ID" = form."VIEWPORT_ID" JOIN "AO_54307E_VIEWPORTFIELD" field ON form."ID" = field."FORM_ID" JOIN "AO_54307E_VIEWPORTFIELDVALUE" fvalue ON field."ID" = fvalue."FIELD_ID" WHERE p.projecttype = 'service_desk' AND field."DISPLAYED" = FALSE AND field."FIELD_ID" = 'security'), security_level_mapping AS (SELECT p.id AS pid, sisl.id AS isl FROM project p JOIN nodeassociation na ON p.id = na.source_node_id JOIN issuesecurityscheme iss ON na.sink_node_id = iss.id JOIN schemeissuesecuritylevels sisl ON iss.id = sisl.scheme WHERE p.projecttype = 'service_desk' AND na.source_node_entity = 'Project' AND na.sink_node_entity = 'IssueSecurityScheme') SELECT * FROM security_form_fields sff WHERE sff.issue_security_level::NUMERIC NOT IN (SELECT slm.isl FROM security_level_mapping slm WHERE slm.pid = sff.project_id);
Repair existing issues
Manually correct the "security" column in the "jiraissue" table.
![]() You can find issues with invalid security levels with this database query:
You can find issues with invalid security levels with this database query:
WITH security_level_mapping AS (SELECT p.id AS pid, sisl.id AS isl FROM project p JOIN nodeassociation na ON p.id = na.source_node_id JOIN issuesecurityscheme iss ON na.sink_node_id = iss.id JOIN schemeissuesecuritylevels sisl ON iss.id = sisl.scheme WHERE p.projecttype = 'service_desk' AND na.source_node_entity = 'Project' AND na.sink_node_entity = 'IssueSecurityScheme') SELECT p.pname AS project_name, p.pkey AS project_key, ji.issuenum AS issue_number, ji.id AS issue_id, ji.security AS issue_security_level, ji.summary AS issue_summary FROM jiraissue ji JOIN project p ON ji.project = p.id WHERE p.projecttype = 'service_desk' AND ji.security IS NOT NULL AND ji.security NOT IN (SELECT slm.isl FROM security_level_mapping slm WHERE slm.pid = p.id);
- is caused by
-
JRASERVER-67812 SecurityLevelSystemField validateParams does not check issue security level is valid for the project
-
- Closed
-
- relates to
-
JRASERVER-74605 Jira rest api allows assigning of a security level from a unrelated issue security scheme
-
- Closed
-
- supersedes
-
JSDSERVER-6672 Changing the Security Scheme can block request types if the Security field is included as hidden
-
- Closed
-
- links to
- mentioned in
-
Page Loading...