-
Type:
Suggestion
-
Resolution: Won't Fix
-
None
-
143
Hi All,
The "JSM Customer" role is designed to explicit access to specific individuals and groups. This role exists to minimise the risk of permissions escalation and unauthorised access to JSM sites and portals.
We suggest two recommended implementations to seamlessly grant your help desk users access:
(1) Configuring "Approved Domains" to assign users the "Customer" role
Approved domains allows admins to grant users the "Customer" role when they interact with your JSM site (this could be via email/portal or any other channel)
When a user interacts with your JSM site and belongs to an "Approved domain" they will be granted the correct level of product access (Based on your "Approved domains" settings). When configured with the "Customer" role they will be able to seamlessly raise requests and access your help center without admins intervening.
(2) Atlassian Access (Guard) SCIM sync Groups via Identity Providers
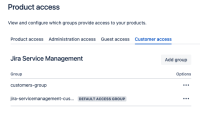
Atlassian is able to sync "groups" from your connected Identity Providers. Using a user group synchronized from the Identity Provider and assigning this group "Customer" access under the Organizations (Admin Hub > Products > Select site > Product access), is the most common method to ensure they are granted this role with immediate access to Open service projects.
These "groups" are synced with your IdP - your users accounts are immediately created and licences are immediately granted.
Both of these options seamlessly grant your users the "Customer" role and access to raise tickets without admins intervening.
If these options aren't appropriate for your JSM setup - Please leave me a comment on this ticket so we can discuss your scenario further
Many thanks,
Ash Young
Product Manager, JSM
Summary
Since the implementation of the Jira Service Management Customer Role, accounts provisioned via Atlassian (SCIM) won't have Customer permissions right off the bat.
Workaround
Companies that need to provision their customers into JSM will need to:
1. Create a new group in their Identity Provider (Okta, Azure, etc)
2. Add everyone they want as a customer to this group.
3. Sync the group into Atlassian Cloud, setting it as an access group for the Jira Service Management - Customer application access.
- is related to
-
ACCESS-1767 Provisioning users with certain application access does not add them to the default access groups for that application
-
- Closed
-
-
ACCESS-604 Grant users synced from identity providers via SCIM application access by default
- Gathering Interest
-
ENT-1999 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
- Wiki Page
-
Wiki Page Loading...