-
Type:
Suggestion
-
Resolution: Fixed
-
Component/s: Forge and Connect
NOTE: This suggestion is for JIRA Service Desk Cloud. Using JIRA Service Desk Server? See the corresponding suggestion.
We use a custom Seraph authenticator / Seraph config to authenticate users against an external Single Sign On process to log in to our JIRA instance.
Standard pages within JIRA (e.g., browsing to a specific issue) correctly respect the Seraph config and redirect unauthenticated users according to the Seraph login.url1 parameter.
Service Desk does not respect this parameter, and instead, prompts unauthenticated users to log in via it's own custom login page (e.g., <server>/servicedesk/customer/portal/1/user/login).
This is problematic for us. Our users who land on the Service Desk provided login page are stuck; their accounts in JIRA do not have passwords set up, so they can never successfully login on this page.
Steps to reproduce expected behavior:
1. Configure JIRA to use a seraph-config.xml Seraph configuration that includes a value for the login.url parameter.
2. Be logged OUT of JIRA.
3. Browse to a secure page not provided by Service Desk, e.g., <server>/browse/DESK-2.
4. Notice that JIRA redirects you to the login page provided in the Seraph configuration
Steps to reproduce wrong behavior:
1. Configure JIRA to use a seraph-config.xml Seraph configuration that includes a value for the login.url parameter.
2. Be logged OUT of JIRA.
3. Browse to a secure page provided by Service Desk, e.g., <server>/servicedesk/customer/portal/1/DESK-2.
4. Notice that JIRA does not redirect you to the login page provided in the Seraph configuration
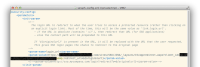
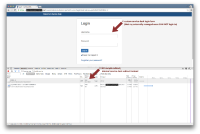
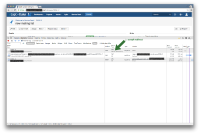
Attached, please find three screenshots:
- A snippet of our seraph-config.xml file
- Network activity when starting un-authenticated, going to a "standard" JIRA page, and having JIRA redirect the user according to the Seraph configuration
- Network activity when starting un-authenticated, going to a Service Desk provided page, and having JIRA (wrongly) redirect the user – not to the Seraph specified location – but to a custom Service Desk login page
- is related to
-
JSDCLOUD-1498 JIRA Service Desk Authentication Documentation
- Closed
-
JSDSERVER-1025 Service Desk login does NOT respect use of custom Seraph Authenticator
- Closed
-
JSDCLOUD-1244 Create a Crowd SSO authenticator that will allow Customers to be authenticated from the local directory
- Reviewing