-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Medium
-
Affects Version/s: 8.13.20, 8.20.7, 8.22.1, 8.22.2
-
Component/s: User Management - Others
-
8.13
-
9
-
Severity 2 - Major
-
8
Issue Summary
This is reproducible on Data Center: yes
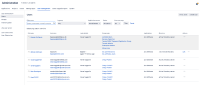
Nested group members not accounted for licensed user count in Jira 8.22.1 from remote directory. This causes challenge for the admin to get a accurate number of licenses available.
The issue is not present for Jira internal directory.
Steps to Reproduce
- Install or upgrade to Jira software 8.22.1
- Setup remote LDAP directory with nested groups enabled.
- Sync the directory
Expected Results
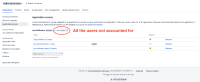
- All the users are accounted towards the license count.
Actual Results
- The licensed user count does not include users which are member of the child group of the group which has application access.
- The users with direct membership to the group which has application access are accounted toward to the license count.
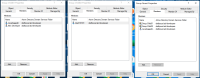
- When we click on the user license count on Application page, it opens the userbrowser page for the application access role (jira software in this case) with the correct number of users listed. Please refer to the screenshots below.


Remote Directory configuration
Current user:
Directory ID: 1
Username: deepswrk
Display name: deepak Sidhpura
Email address: dsidhpura@atlassian.com
Directory 1:
Directory ID: 1
Name: Jira Internal Directory
Active: true
Type: INTERNAL
Created date: Thu Feb 28 11:57:51 IST 2013
Updated date: Thu Feb 28 11:57:51 IST 2013
Allowed operations: [CREATE_GROUP, CREATE_ROLE, CREATE_USER, DELETE_GROUP, DELETE_ROLE, DELETE_USER, UPDATE_GROUP, UPDATE_GROUP_ATTRIBUTE, UPDATE_ROLE, UPDATE_ROLE_ATTRIBUTE, UPDATE_USER, UPDATE_USER_ATTRIBUTE]
Implementation class: com.atlassian.crowd.directory.InternalDirectory
Encryption type: atlassian-security
Attributes:
user_encryption_method: atlassian-security
Directory 2:
Directory ID: 10000
Name: Active Directory server
Active: true
Type: CONNECTOR
Created date: Mon Apr 18 12:48:29 IST 2022
Updated date: Mon Apr 18 12:49:13 IST 2022
Allowed operations: [CREATE_GROUP, DELETE_GROUP, UPDATE_GROUP, UPDATE_GROUP_ATTRIBUTE, UPDATE_USER_ATTRIBUTE]
Implementation class: com.atlassian.crowd.directory.MicrosoftActiveDirectory
Encryption type: sha
Attributes:
autoAddGroups:
com.atlassian.crowd.directory.sync.currentstartsynctime: 1650266353262
com.atlassian.crowd.directory.sync.issynchronising: false
com.atlassian.crowd.directory.sync.lastdurationms: 80
com.atlassian.crowd.directory.sync.laststartsynctime: 1650266353262
crowd.sync.group.membership.after.successful.user.auth.enabled: only_when_first_created
crowd.sync.incremental.enabled: true
directory.cache.synchronise.interval: 3600
ldap.basedn: dc=dsidhpura,dc=lab
ldap.connection.timeout: 10000
ldap.external.id: objectGUID
ldap.filter.expiredUsers: true
ldap.group.description: description
ldap.group.dn:
ldap.group.filter: (objectCategory=Group)
ldap.group.name: cn
ldap.group.objectclass: group
ldap.group.usernames: member
ldap.local.groups: true
ldap.nestedgroups.disabled: false
ldap.pagedresults: true
ldap.pagedresults.size: 1000
ldap.password: ********
ldap.pool.initsize: null
ldap.pool.maxsize: null
ldap.pool.prefsize: null
ldap.pool.timeout: 0
ldap.propogate.changes: false
ldap.read.timeout: 120000
ldap.referral: false
ldap.relaxed.dn.standardisation: true
ldap.roles.disabled: true
ldap.search.timelimit: 60000
ldap.secure: false
ldap.url: ldap://windc01.dsidhpura.lab:389
ldap.user.displayname: displayName
ldap.user.dn:
ldap.user.email: mail
ldap.user.encryption: sha
ldap.user.filter: (&(objectCategory=Person)(mail=*))
ldap.user.firstname: givenName
ldap.user.group: memberOf
ldap.user.lastname: sn
ldap.user.objectclass: user
ldap.user.password: unicodePwd
ldap.user.username: mail
ldap.user.username.rdn: cn
ldap.userdn: dsidhpura\deepaks
ldap.usermembership.use: false
ldap.usermembership.use.for.groups: false
localUserStatusEnabled: false
![]() The users ability to login to JSM is not impacted by this. Which leads to a challenge of getting accurate count of license stil available for assignment.
The users ability to login to JSM is not impacted by this. Which leads to a challenge of getting accurate count of license stil available for assignment.
Workaround
Currently there is no known workaround for this behavior. A workaround will be added here when available
- relates to
-
JRASERVER-73875 User Directory fails sync with error :Error occurred while refreshing the cache for directory
-
- Closed
-
-
JRASERVER-72161 License count for nested group users are counted towards the license although nested group is disabled.
-
- Closed
-
-
HL-2802 Loading...