-
Bug
-
Resolution: Not a bug
-
Low
-
None
-
4.13.0, 4.20.13
-
3
-
Severity 2 - Major
-
Steps to Reproduce
- In JSD project A, set the customer permission as "Who can access the portal and send requests to <project key>?": "Customers my team adds to the project"
- Confirm that the project has no customers added
- Access the portal by a customer that has access to customer portal (customer that is added to another project B but not project A). The customer is not able to access the portal and receives the error: "You do not have permission to view this Portal."
- Add a request type in project A and some custom fields in that request type (these are considered sensitive data). The custom fields should be part of the "Create issue" screen.
- Edit the permission scheme to add one of these fields "Browse Project" permission in project A:
- Reporter
- Single user
- Current assignee
- User custom field value
- Group custom field value
- Access the portal by the same customer that has access to the customer portal (customer that is added to another project B but not project A).
Expected Results
Customer will only see project B.
Actual Results
The customer sees project B and can browse request types and see custom fields (Testers in my example) associated with project A (created in step 4 above).
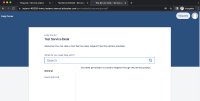
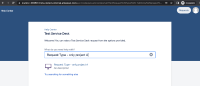
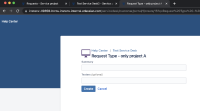
P.S: The customer sees "You need permission to create a request through this service project." this time.
Workaround
Remove all these entries from the "Browse Project" permission:
- Reporter
- Single user
- Current assignee
- User custom field value
- Group custom field value
- is cloned from
-
JSDCLOUD-8167 "Browse Project" permission set for Reporter overrides the customer permission that results the project getting exposed in the customer portal
-
- In Progress
-
- relates to
-
JSDSERVER-12210 There was a problem completing the current request error message while linking a KB from Jira OnPrem to Confluence Cloud
-
- Closed
-
- mentioned in
-
 Page Failed to load
Page Failed to load
| Form Name | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
[JSDSERVER-12130] "Browse Project" permission set to specific values overrides the customer permission that results in the project getting exposed in the customer portal
| Assignee | New: Anton Sidliar [ 3774f29b04e6 ] |
| Resolution | New: Not a bug [ 12 ] | |
| Status | Original: Long Term Backlog [ 12073 ] | New: Closed [ 6 ] |
| Support reference count | Original: 2 | New: 3 |
| Support reference count | Original: 1 | New: 2 |
| Status | Original: Gathering Impact [ 12072 ] | New: Long Term Backlog [ 12073 ] |
| Status | Original: Needs Triage [ 10030 ] | New: Gathering Impact [ 12072 ] |
| Resolution | Original: Tracked Elsewhere [ 15 ] | |
| Status | Original: Closed [ 6 ] | New: Needs Triage [ 10030 ] |
| Security | Original: Atlassian Staff [ 10750 ] |
c8bcca445054 as you resolved this issue with "Not a bug" - but JSDCLOUD-8167 still being unresolved and the bug still being present on LTS 9.12.x - will this security issue ever be fixed and if so, how will will be notified about this?
We recently had a security incident regarding this.