Issue Summary
XSRF checks were added to the endpoint /rest/collectors/1.0/template/custom as part of the fix for JRASERVER-73068
The server receives requests from the same origin, as the form page is the same origin as the form submission, thus, the XSRF HTTP header matches, which is fine.
However for the XSRF check to succeed, the form token and cookie token sent to the server must match. The problem occurs because modern web browser (beginning Chrome 80+) do not accept the atlassian.xsrf.cookie initially sent by the server in an iframe as it is treated as cross-site and is therefore rejected. This is because the cookie does not have the Same-Site:None attribute set (see JRASERVER-70494).
Steps to Reproduce
- Create a Jira 8.20.3, a sample SCRUM project, and an issue collector (custom type)
- Insert the sample code into a html page on the same site (for testing local, JIRA_INSTALL/atlassian-jira/static-assets/test.html is fine)
- Load the page (eg http://JUPITER/static-assets/test.html), and submit an issue with the collector. Note that the POST to /rest/collectors/1.0/template/custom succeeds
- Insert the sample code into a html page on your local machine (differing origin), and load it in your browser
Expected Results
The issue submission succeeds
Actual Results
- The POST to /rest/collectors/1.0/template/custom is rejected with HTTP 404 and body "XSRF check failed"
- Error is presented to the client
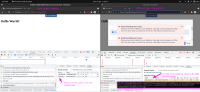
 Oops - something went wrong...
Oops - something went wrong...
There was a problem submitting your feedback, likely due to the configuration of this form. You might want to contact the site owner to let them know about this issue
When enabling Jira Admin -> System -> Logging and Profiling -> HTTP Access log (ON) -> HTTP Dump Log (ON), the response from the client can be observed in JIRA_HOME/log/atlassian-jira-http-dump.log. Observe that the client does not sent the XSRF token in the cookie, as the browser rejected storing it
Workaround
The following workaround will disable XSRF checks for the issue collector, which was the behaviour prior to JRASERVER-73068. This may be tolerable for you, but it's worthwhile confirming within your organisation
Modify the reverse proxy / load balancer / WAF to add the following header to the request as it makes it's way to the Jira node:
- Condition: Method: POST
- Condition: Request URL: /rest/collectors/1.0/template/custom/*
- Action: Add header: X-Atlassian-Token: no-check
Note on fix
We've added "SameSite=None" parameter to xsrftoken, which is on by default.
Please note ![]() : fix works only if connection is secure, issue collector needs to access Jira through https protocol. If it is not, collector works properly only on firefox.
: fix works only if connection is secure, issue collector needs to access Jira through https protocol. If it is not, collector works properly only on firefox.
Unfortunately we can't omit this restriction, because that's how cookies are handled on chrome, opera etc. and they don't allow setting SameSite=None parameter to cookies if connection is not secure.
Note that the reverse proxy needs to allow the SameSite cookie (SameSite="none") and the secure="true" attribute needs to be present in the Tomcat connector (server.xml). This is required so that the HTTP response sets the cookie parameters correctly.
- is caused by
-
JRASERVER-73068 Reflected XSS via /rest/collectors/1.0/template/custom - CVE-2021-43942
-
- Published
-
- is related to
-
JRASERVER-70494 Issue Collectors won't work for clients using Chrome 80 which enables new samesite cookie controls
-
- Closed
-
-
JSWSERVER-25463 Give Feedback form is failing in Chrome
-
- Gathering Impact
-
-
JRASERVER-70471 Implement SameSite policy support
- Gathering Interest
-
RAID-2850 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
- relates to
-
RAID-2826 Loading...