-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Low
-
Affects Version/s: 10.99.3
-
Component/s: Enterprise Design|Administration|Navigation
-
Severity 3 - Minor
-
No
Issue Summary
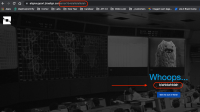
- Any anonymous user is able to craft and supply a query string to the Whoops (error.asp) page
- The error.asp page seems to ingest & process any payload sent (given the string is shown in the Whoops screen)
Steps to Reproduce
- As an anonymous user, craft a query string like the example below:
https://<instance>.jiraalign.com/error?d=<user-supplied input> - By using Mozilla, browse to that URL
Expected Results
Customer's Expected Behavior
- Anonymous users should not be able to parse/inject any payload via any ASP page
- Logged-in users should not be able to parse/inject any payload via https://<instance>.jiraalign.com/error?d=<user-supplied input>
Actual Results
Workaround
- Currently there is no known workaround for this behavior. A workaround will be added here when available