-
Type:
Suggestion
-
Resolution: Unresolved
-
Component/s: Repository - Pull requests, Repository - Settings Workflow
-
23
Summary: My (developer, non-admin) team needs the ability to create and merge (after getting PR approvals) release/* & hotfix/* branches. My team should not be able to push directly to develop, master, hotfix/* or release/* branches.
According to the documentation, that should not be a problem.
I think there's a bug.
Here's why:
According to this documentation, Branch Permissions should not prevent users from creating a branch:
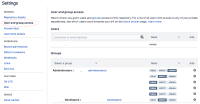
Repository write permissions exist for the group we need this functionality for:
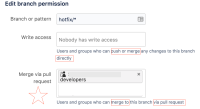
This describes exactly what we need:
But when we set it to that, we can no longer create a branch:
(yes I'd normally create a hotfix from master, but this was a test)
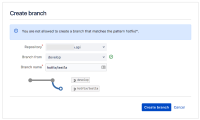
Please help. For auditing purposes, it is very important that no one can accidentally push to these branches directly.
Thanks in advance!!!
- is duplicated by
-
BCLOUD-21619 Allow users to create branches but prevent commits without PR
- Closed
- is related to
-
BCLOUD-20672 Ability to create a destination branch on successful approval of a pull request
- Closed