-
Suggestion
-
Resolution: Unresolved
-
812
-
Problem Definition
When User Provisioning is enabled in the identity provider, created users through push group from the IdP are just added to the synced group in the Cloud site and not to the default application access group(s).
This creates a problem when the Cloud instance has a lot of existing projects/spaces with access already granted to default app groups.
Workarounds
There are currently a few possible workarounds for admins:
- The admin(s) would need to manually grant synced IdP groups access to existing Jira projects / Confluence spaces OR manually add the users to the default app group on Atlassian side. Which is a time-consuming process if there are a lot of projects/spaces in the instance.
- RECOMMENDED: The admin(s) would need to configure the synced group from the IDP to grant product licenses and permissions with the same configuration as the default group (can be time-consuming depending on how many places the default group has been given access to).
- The admin(s) can configure the Approved Domain settings (see the Approved Domain support doc), to allow users with their email domain to get access to the necessary products as needed. These users will be put into the default product access groups.
- The out of the box default groups (such as jira-software-users-sitename) can be taken over by the IdP.
- Create a new group, e.g. default-jira-software-users-sitename, and make it the default group for your product.
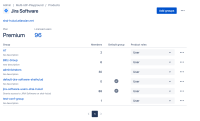
- For the standard default group (e.g. jira-software-users-sitename), remove it as the default group for your product.
- Create a group in your IdP with the standard default group name (e.g. jira-software-users-sitename) and sync your users who need product access into this group.
- The group will be 'taken over' by your IdP, the users will sync from your IdP, but the project/space settings will be kept as is.
- Create a new group, e.g. default-jira-software-users-sitename, and make it the default group for your product.
In case additional support is required, please raise a ticket with Atlassian Support.
- is duplicated by
-
ACCESS-1767 Provisioning users with certain application access does not add them to the default access groups for that application
-
- Closed
-
-
ACCESS-982 Allow syncing users to local Product Default Access Group over SCIM
- Closed
-
ACCESS-1397 Sync group membership from local default group to synced group
- Gathering Interest
- relates to
-
JSDCLOUD-12954 Provisioned accounts should have Customer access by default
- Closed
- blocks
-
ACE-3234 You do not have permission to view this issue
- is related to
-
ENT-1283 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
| Form Name | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
vv this is the exact same problem we're having. +1!