-
Type:
Bug
-
Resolution: Unresolved
-
Priority:
Low
-
None
-
Affects Version/s: None
-
Component/s: SSO
-
None
Issue Summary
This is reproducible on Data Center: yes
Steps to Reproduce
- Configure SAML, fill in all fields
- For the Username mapping, input a value longer than 255 characters
- Example:
${uiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduiduid}
- Example:
- Save Configuration
Tested fields and Behaviour
I tested the following fields and although all of them produced a database error from PostgreSQL, some of the fields did not result in a corrupt configuration and simply failed to save. Other fields did result in a corrupt configuration.
- Name: Resulted in database exception, but no corrupt data was added. The "Authentication methods" was still accessible
- Single sign-on issuer: Resulted in database exception, but no corrupt data was added. The "Authentication methods" was still accessible
- Identity provider single sign-on URL: Resulted in database exception and added the corrupted data into database. The "Authentication methods" was no longer accessible.
- Username mapping: Resulted in database exception and added the corrupted data into database. The "Authentication methods" was no longer accessible.
Expected Results
Jira has a validation check for the fields and will prevent the configuration from being saved.
Actual Results
- Jira has no check. It attempts to insert the data into the database.
- Database is configured for "character varying(255)" and throws an exception
- SAML configuration is corrupt in the database
- It is no longer possible to access SAML configurations from Jira's GUI
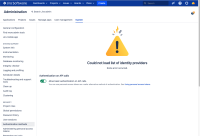
The below exception is thrown in the atlassian-jira.log file when initially trying to save the configuration:
2022-10-27 17:06:37,903+0000 http-nio-8080-exec-8 ERROR admin 1026x209x1 wamxy2 172.29.245.101,172.50.0.3 /rest/authconfig/1.0/idps [c.a.p.r.c.error.jersey.ThrowableExceptionMapper] Uncaught exception thro wn by REST service: null java.lang.reflect.UndeclaredThrowableException at com.sun.proxy.$Proxy3943.save(Unknown Source) at com.atlassian.plugins.authentication.impl.config.SsoConfigDao.saveSamlConfig(SsoConfigDao.java:289) at com.atlassian.plugins.authentication.impl.config.SsoConfigDao.saveIdpConfig(SsoConfigDao.java:144) at com.atlassian.plugins.authentication.impl.config.IdpConfigServiceImpl.updateIdpConfigInternal(IdpConfigServiceImpl.java:190) at com.atlassian.plugins.authentication.impl.config.IdpConfigServiceImpl.addIdpConfig(IdpConfigServiceImpl.java:96) at com.atlassian.plugins.authentication.impl.config.AuditingIdpConfigService.addIdpConfig(AuditingIdpConfigService.java:121) at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) at com.atlassian.activeobjects.tx.TransactionalProxy.invoke(TransactionalProxy.java:57) at com.atlassian.activeobjects.tx.TransactionalProxy.lambda$executeInTransaction$0(TransactionalProxy.java:47) at com.atlassian.sal.core.transaction.HostContextTransactionTemplate$1.doInTransaction(HostContextTransactionTemplate.java:21) at com.atlassian.jira.DefaultHostContextAccessor.doInTransaction(DefaultHostContextAccessor.java:50) at jdk.internal.reflect.GeneratedMethodAccessor245.invoke(Unknown Source) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) at com.atlassian.plugin.util.ContextClassLoaderSettingInvocationHandler.invoke(ContextClassLoaderSettingInvocationHandler.java:26) at com.sun.proxy.$Proxy682.doInTransaction(Unknown Source) at jdk.internal.reflect.GeneratedMethodAccessor245.invoke(Unknown Source) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) at com.atlassian.plugin.osgi.bridge.external.HostComponentFactoryBean$DynamicServiceInvocationHandler.invoke(HostComponentFactoryBean.java:130) at com.sun.proxy.$Proxy682.doInTransaction(Unknown Source) at com.atlassian.sal.core.transaction.HostContextTransactionTemplate.execute(HostContextTransactionTemplate.java:18) at jdk.internal.reflect.GeneratedMethodAccessor264.invoke(Unknown Source) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) ... ... Caused by: org.postgresql.util.PSQLException: ERROR: value too long for type character varying(255) at org.postgresql.core.v3.QueryExecutorImpl.receiveErrorResponse(QueryExecutorImpl.java:2565) at org.postgresql.core.v3.QueryExecutorImpl.processResults(QueryExecutorImpl.java:2297) at org.postgresql.core.v3.QueryExecutorImpl.execute(QueryExecutorImpl.java:322) at org.postgresql.jdbc.PgStatement.executeInternal(PgStatement.java:481) at org.postgresql.jdbc.PgStatement.execute(PgStatement.java:401) at org.postgresql.jdbc.PgPreparedStatement.executeUpdate(PgPreparedStatement.java:130) at org.apache.commons.dbcp2.DelegatingPreparedStatement.executeUpdate(DelegatingPreparedStatement.java:98) at org.apache.commons.dbcp2.DelegatingPreparedStatement.executeUpdate(DelegatingPreparedStatement.java:98) at com.atlassian.jira.ofbiz.sql.PreparedStatementWrapper.executeUpdate(PreparedStatementWrapper.java:47) at com.atlassian.jira.diagnostic.connection.DiagnosticPreparedStatement.lambda$executeUpdate$7(DiagnosticPreparedStatement.java:69) at com.atlassian.diagnostics.internal.platform.monitor.db.DefaultDatabaseDiagnosticsCollector.recordExecutionTime(DefaultDatabaseDiagnosticsCollector.java:104) at com.atlassian.jira.diagnostic.connection.DatabaseDiagnosticsCollectorDelegate.recordExecutionTime(DatabaseDiagnosticsCollectorDelegate.java:62) at com.atlassian.jira.diagnostic.connection.DiagnosticPreparedStatement.executeUpdate(DiagnosticPreparedStatement.java:69) at net.java.ao.ForwardingPreparedStatement.executeUpdate(ForwardingPreparedStatement.java:45) at net.java.ao.ParameterMetadataCachingPreparedStatement.executeUpdate(ParameterMetadataCachingPreparedStatement.java:10) at net.java.ao.EntityProxy.save(EntityProxy.java:574) at net.java.ao.EntityProxy.invoke(EntityProxy.java:116) ... 356 more
After the above occurs, loading Jira's Authentication methods admin page results in the below exception atlassian-jira.log file:
2022-10-27 17:10:29,851+0000 http-nio-8080-exec-6 ERROR admin 1030x248x3 wifcc 172.29.245.101,172.50.0.3 /rest/authconfig/1.0/idps [c.a.p.r.c.error.jersey.ThrowableExceptionMapper] Uncaught exception throw n by REST service: Unknown SSO type: null java.lang.IllegalStateException: Unknown SSO type: null at com.atlassian.plugins.authentication.impl.config.SsoConfigDao.lambda$mapIdpConfig$1(SsoConfigDao.java:161) at java.base/java.util.Optional.orElseThrow(Optional.java:408) at com.atlassian.plugins.authentication.impl.config.SsoConfigDao.mapIdpConfig(SsoConfigDao.java:161) at java.base/java.util.stream.ReferencePipeline$3$1.accept(ReferencePipeline.java:195) at java.base/java.util.Spliterators$ArraySpliterator.forEachRemaining(Spliterators.java:948) at java.base/java.util.stream.AbstractPipeline.copyInto(AbstractPipeline.java:484) at java.base/java.util.stream.AbstractPipeline.wrapAndCopyInto(AbstractPipeline.java:474) at java.base/java.util.stream.ReduceOps$ReduceOp.evaluateSequential(ReduceOps.java:913) at java.base/java.util.stream.AbstractPipeline.evaluate(AbstractPipeline.java:234) at java.base/java.util.stream.ReferencePipeline.collect(ReferencePipeline.java:578) at com.atlassian.plugins.authentication.impl.config.SsoConfigDao.getIdpConfigs(SsoConfigDao.java:96) at com.atlassian.plugins.authentication.impl.config.IdpConfigServiceImpl.getIdpConfigs(IdpConfigServiceImpl.java:65) at com.atlassian.plugins.authentication.impl.config.AuditingIdpConfigService.getIdpConfigs(AuditingIdpConfigService.java:89) at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method) at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) at com.atlassian.activeobjects.tx.TransactionalProxy.invoke(TransactionalProxy.java:57) at com.atlassian.activeobjects.tx.TransactionalProxy.lambda$executeInTransaction$0(TransactionalProxy.java:47) at com.atlassian.sal.core.transaction.HostContextTransactionTemplate$1.doInTransaction(HostContextTransactionTemplate.java:21) at com.atlassian.jira.DefaultHostContextAccessor.doInTransaction(DefaultHostContextAccessor.java:50) at jdk.internal.reflect.GeneratedMethodAccessor245.invoke(Unknown Source) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566)
Workaround
- Access the database and locate the corrupt SAML configuration:
select * from "AO_ED669C_IDP_CONFIG";- The corrupt entry will have many required columns that are empty. Such as: SAML_IDP_TYPE, SIGNING_CERT, SSO_TYPE, SSO_URL, USERNAME_ATTRIBUTE, etc.
- Delete the corrupt entry.
- is duplicated by
-
JRASERVER-74463 Corrupt SAML Configuration when using Values that are too Long
-
- Closed
-
- is cloned by
-
KRAK-4852 Loading...