-
Bug
-
Resolution: Unresolved
-
Medium (View bug fix roadmap)
-
None
-
8.20.7, 8.20.8
-
8.2
-
4
-
Severity 2 - Major
-
0
-
Issue Summary
WAF would be blocking file upload because in Jira the file upload is marked as “text/html” and the WAF uses the Inspect request body feature enabled by default which stops the file upload.
However, using the “multipart/form-data“ which is the only acceptable type according to WAF to mark it as a successful file upload instead of the request body.
This is reproducible on Data Center: yes
Steps to Reproduce
- Setup an Azure instance and install Jira
- Make sure Jira runs on HTTPS
- Secure this instance with WAF (Web Application Firewall)
- Under Policy Settings of this WAF turn on the "Inspect Request Body" option
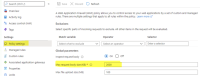
- Save the configuration and try to upload a file
Expected Results
Looking for a solution to have all file uploads forced as content-type "multipart/form-data" so that we can have the body inspection working in the Application Gateway WAF settings.
Actual Results
Files over 128KB will fail during upload since the application gateway will interpret any header that is not "multipart/form-data" as a body and not a file upload.
Basically, the behavior of Jira is that the content type of the uploaded file will be set by the browser which gives a lot of different content types.
Workaround
Workaround is to turn off the Inspect request body to off.
However, by setting Inspect request body off, the request bodies of all traffic won't be evaluated by your WAF. This may be useful if you know that the request bodies aren’t malicious to your application.
When you disable this option, only the request body isn't inspected. The headers and cookies remain inspected unless individual ones are excluded using the exclusion list functionality.
| Form Name | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|