-
Type:
Bug
-
Resolution: Not a bug
-
Priority:
Medium
-
None
-
Affects Version/s: 10.5.0, 10.5.1, 10.6.0
-
Component/s: Upgrade
-
None
-
10.05
-
6
-
Severity 2 - Major
-
21
-
Issue Summary
When the startup parameter -Datlassian.secret.service.state=disabled is set, after an upgrade (or running "docker run...") external directories are not able to sync, nor are their passwords able to be updated.
Steps to Reproduce
- Have a Jira instance with an external directory attached
- Stop Jira
- Add the startup parameter -Datlassian.secret.service.state=disabled
- Run a Jira upgrade (or a docker run... for docker instances)
Expected Results
Jira will start successfully, the associated passwords remain unencrypted, and LDAP logins and synchronizations continue to be successful
Actual Results
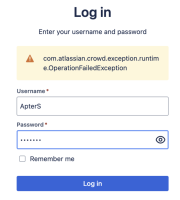
LDAP won't sync, causing logins via the LDAP directory to fail and generating an error on the login page of "com.atlassian.crowd,exception.runtime.OperationFailedException".

Additionally, attempting to update the LDAP password in the UI fails (though just running a test will succeed)
Relevant Information
Please refer to the following KB articles to learn more about encryption in Jira
Workaround
Removing the startup parameter, starting Jira, and resaving the password on the LDAP directory allows the directory to sync once again.
![]() This will cause the associated passwords to be encrypted on restart
This will cause the associated passwords to be encrypted on restart
- is related to
-
JRASERVER-78634 Jira 10 upgrade task ( UpgradeTask_Build10020000 ) fails to convert/encrypt LDAP credentials if username and password are blank
-
- Gathering Impact
-
- relates to
-
JRASERVER-78897 Creating/updating user directories ignores state of secure secret storage
-
- Closed
-
- mentioned in
-
Page Loading...