-
Type:
Bug
-
Resolution: Not a bug
-
Priority:
Low
-
None
-
Affects Version/s: 5.2
-
Component/s: None
-
5.02
Steps to Reproduce:
Follow all the steps to generate a self-signed certificate as described in Running JIRA over SSL or HTTPS.
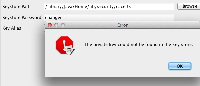
When you try to use the set the certificate path in the JIRA Configuration Tool the following is shown:

It's complaining about the lack of the Private Key, but the key is where it should be in the User's root directory:
laptop:~ pcora$ keytool -list -alias tomcat -keystore ~/.keystore Enter keystore password: tomcat, Nov 19, 2012, PrivateKeyEntry, Certificate fingerprint (MD5): 00:A0:94:5C:B7:BB:FD:D9:D1:BC:8D:46:03:80:5E:02
And also the trustedCertEntry:
laptop:~ pcora$ keytool -list -alias tomcat -keystore $JAVA_HOME/lib/security/cacerts Enter keystore password: tomcat, Nov 19, 2012, trustedCertEntry, Certificate fingerprint (MD5): 00:A0:94:5C:B7:BB:FD:D9:D1:BC:8D:46:03:80:5E:02
Actual Results:
Using the JIRA Configuration Tool prevents you to properly configure SSL in JIRA.
Expected Results:
The user places the Key Store path and JIRA accepts it.
Workaround:
Follow the old way to configure, which is described in http://confluence.atlassian.com/display/JIRA051/Running+JIRA+over+SSL+or+HTTPS
OR
Generate key and import it to the keystore using one line command(to avoid exporting and importing):
keytool -genkey -alias <your_preferred_alias> -keyalg RSA -keystore <location_to_keystore>
- relates to
-
JRASERVER-28624 Import Certificate into the Trust-store discrepencies between versions
- Closed