-
Type:
Bug
-
Resolution: Answered
-
Priority:
Highest
-
None
-
Affects Version/s: 4.2
-
Component/s: User Management - Others
-
4.02
Security auditing tests performed on a Jira Bug Issue and Project Tracking Software locally running instance shown that at least two vulnerabilities regarding User Enumeration were found within the software.
Case 1: Logged In
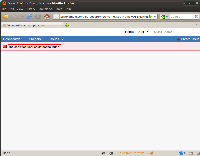
Whenever a logged user accesses the Url [/jira/secure/ViewProfile.jspa?name=USERNAME] with parameter name filled with a non existent user of the system, the message: "The specified user could not be found." is shown. This vulnerability grants the possibility for a low level privileged user to enumerate other users of the system — including higher level privileged users. The image below describes this behavior:

Case 2: Unlogged
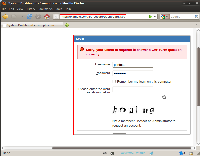
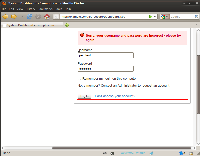
From the main login page it is possible to enumerate system users by inserting wrong passwords three times. This procedure triggers a CAPTCHA verification for that user. However, the CAPTCHA verification doesn't appear for non existant users. The first image below describes this behavior, the second one describes the lack of it.


Disclaimer: A thorough scan may be done to find out if the CAPTCHA function is a mandatory feature or if it can be disabled. If it can, Case 2 shouldn't be a enumeration.
- relates to
-
JRACLOUD-65725 Username enumeration using the Login page in OnDemand
-
- Closed
-
-
JRASERVER-71899 Usernames are exposed in the URL while accessing user profiles
-
- Gathering Impact
-
- mentioned in
-
Page Loading...