-
Type:
Suggestion
-
Resolution: Won't Fix
-
None
-
Component/s: None
NOTE: This suggestion is for JIRA Server. Using JIRA Cloud? See the corresponding suggestion.
A clickjacking attack on JIRA would most likely take the form of a third-party site, containing an invisible iframe on top of an unrelated page. The iframe would contain a page in JIRA. The victim would believe he was clicking on the other site but would actually be clicking in JIRA and performing actions he didn't intend.
It enables attackers to perform many actions in our apps, provided that:
- The victim has an active session or "remember me" is set, and
- The victim can be tricked into clicking or typing into an innocent-looking page element on a third-party site.
It requires no XSS vulnerability in JIRA in order to exploit.
Twitter's solution to this was to include a line of JavaScript at the top of every page to break out of frames. This might not work as a broad-scale solution for us (GreenHopper and gadgets both use iframes legitimately) but could be used for administration pages at least.
This threat could be partially mitigated by requiring two clicks for any major administration action. e.g. Currently you can go directly to the project deletion confirmation page and delete a project in one click. If the confirmation page was also XSRF-protected (not just the deletion action itself), it would behave the same for an end-user but would be harder for an attacker to exploit.
-----------
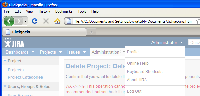
Example attack: This button on some random website gives no indication of malice:

But clicking on it actually deletes a project in JIRA:

The example HTML for this attack is attached; just insert the ID of the project you want to delete into the iframe URL, and use with caution!
- relates to
-
JRACLOUD-21101 JIRA is vulnerable to clickjacking attacks
- Closed