-
Type:
Suggestion
-
Resolution: Fixed
-
Component/s: None
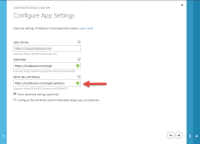
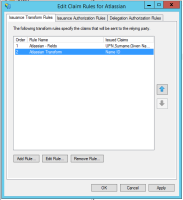
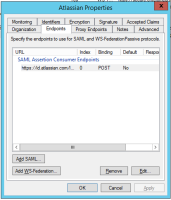
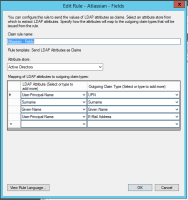
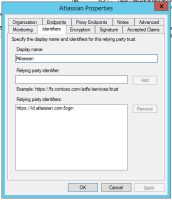
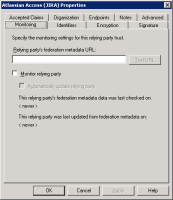
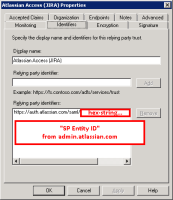
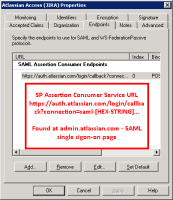
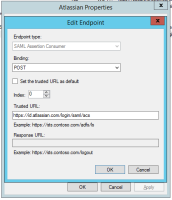
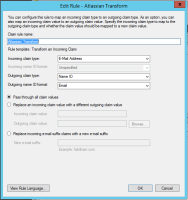
SAML single sign-on is available as part of Identity Manager. More information about Identity Manager.
Read up on how to configure SAML single sign-on for our Cloud products.
Thanks for all of your feedback and discussion on this ticket. We'll continue to monitor and respond to it, as well as take on board your requests for future enhancements.
We receive a lot of requests for new features and improvements, so if you'd like to better understand how we make roadmap decisions, please read: https://confluence.atlassian.com/display/DEV/Implementation+of+New+Features+Policy
- incorporates
-
ID-87 Allow SSO from SAML 2.0 Compliant Software Such As ADFS
- Closed
- is blocked by
-
ID-6177 Support for Exchange/Outlook avatar and account information integration with Confluence users
- Closed
-
ID-6169 Option to lock user out after maximum failed password attempts
- Closed
- is cloned from
-
ID-79 Support LDAP integration with Cloud
- Closed
- is duplicated by
-
ID-112 Single Sign-On support for JIRA OnDemand besides Google Apps
- Closed
- is related to
-
ID-215 External SSO (Single Sign On) integration with Atlassian ID?
- Closed
-
ID-1156 Provide SSO Integration with Office 365
- Closed
-
CEO-1001 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...