-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Medium
-
Affects Version/s: None
-
Component/s: None
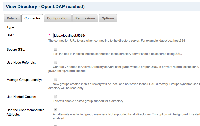
Setting User Membership Attribute allows to gather membership and is respected during full sync.
Unfortunately when user is logged in, his groups are cleared.
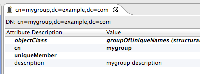
Before login (after full sync):

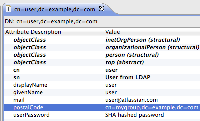
After login:

My local ldap config (I've usted postalCode from my LDAP as a group marker):

- derived from
-
CWD-3429 As an admin, I want external user details synchronised during login
- Closed
- is related to
-
CONFSERVER-31338 Login removes user from all dynamic LDAP groups
-
- Closed
-
- was cloned as
-
JRASERVER-36555 Full LDAP does not respect "User Membership Attribute" during login
-
- Closed
-
- is cloned by
-
JDEV-26451 Loading...
- mentioned in
-
Page Loading...
- relates to
-
CWDDEV-142 Loading...