-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Low
-
Affects Version/s: 7.13.5, 7.18.3
-
Component/s: Server - Authentication
-
1
-
Severity 3 - Minor
Issue Summary
When hitting the resetuserpassword.action URL directly with a username value, it's possible to identify valid users through the responses given by Confluence. The response for a valid user differs from the response for an invalid user.
This is an issue as a malicious entity can harvest user accounts and make it easier to phish, brute force guessing of passwords, or intentionally lock valid users out of their accounts.
Steps to Reproduce
These messages can be reproduced by visiting the following URL for resetting passwords:
http://<CONFLUENCE-URL>/resetuserpassword.action?username=<USERNAME>
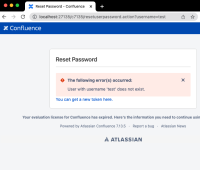
Non-Valid User
When supplied with a non-existent user, Confluence will provide the following error:
(!) The following error(s) occurred:
User with username '<*USERNAME*>' does not exist.
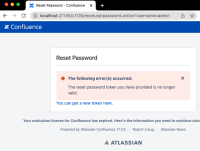
Valid User
When supplied with a valid user, Confluence will provide the following message:
(!) The following error(s) occurred:
The reset password token you have provided is no longer valid.
Expected Results
Confluence should provide a generic response so that it is not possible to tell which usernames are valid users.
Workaround
There is currently no workaround for this issue. If one is found, this ticket will be updated with those steps.
- follows
-
VULN-928421 Loading...
- links to