The fix for this bug has been released to our Long Term Support release.
The fix for this bug is now available in the latest release of Confluence 7.13 and 7.19
Suggestion
IMDSv2 requires token generation to access metadata: Retrieve instance metadata
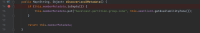
AWS node discovery does not account for this and results in errors like the following:
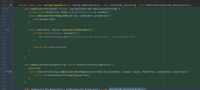
2021-04-01 16:56:09,435 ERROR [Catalina-utility-1] [atlassian.confluence.setup.ConfluenceConfigurationListener] contextInitialized An error was encountered while bootstrapping Confluence (see below): Unable to lookup role in URI: http://169.254.300.300/latest/meta-data/placement/availability-zone/ com.hazelcast.config.InvalidConfigurationException: Unable to lookup role in URI: http://169.254.300.300/latest/meta-data/placement/availability-zone/ at com.hazelcast.aws.utility.MetadataUtil.retrieveMetadataFromURI(MetadataUtil.java:78) at com.hazelcast.aws.utility.MetadataUtil$1.call(MetadataUtil.java:109) at com.hazelcast.aws.utility.MetadataUtil$1.call(MetadataUtil.java:106) at com.hazelcast.aws.utility.RetryUtils.retry(RetryUtils.java:52) at com.hazelcast.aws.utility.MetadataUtil.retrieveMetadataFromURI(MetadataUtil.java:106) at com.hazelcast.aws.AWSClient.getAvailabilityZone(AWSClient.java:62) at com.hazelcast.aws.AwsDiscoveryStrategy.discoverLocalMetadata(AwsDiscoveryStrategy.java:138) at com.hazelcast.spi.discovery.impl.DefaultDiscoveryService.discoverLocalMetadata(DefaultDiscoveryService.java:88) at com.hazelcast.instance.Node.mergeEnvironmentProvidedMemberMetadata(Node.java:555) at com.hazelcast.instance.Node.start(Node.java:401) ...
IMDSv2 would provide greater security from SSRF attacks for customers using IMDSv1
Workaround
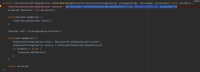
The security concerns around IMDSv1 can be mitigated by using TCP/IP discovery for Hazelcast within Confluence.
- blocks
-
ITPLT-637 Loading...
- is related to
-
PSR-744 Loading...
- Mentioned in
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
- Wiki Page
-
Wiki Page Loading...