-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Medium
-
Affects Version/s: 5.9.12
-
Component/s: Content - Attachments
-
Severity 2 - Major
From an external report:
Confluence recently has been tested and, as a result, we were able to verify the existence of at least one persistent XSS vulnerability. This vulnerability is present in the Edit Attachment feature — specifically in the newFileName field — accessible through the following URL:
https://confluence/pages/editattachment.action
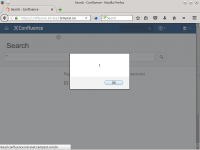
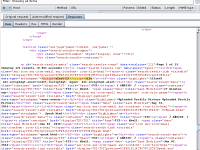
As a means to prove the concept proposed by this issue, we added the value "<script>alert(1)</script>file" (without quotes) in the newFileName field. Such as described in the image named xss.png (attached).
After the aforementioned insertion, the script executes successfully whenever a user visits the vulnerable page, which in turn, is available at:
https://confluence/dosearchsite.action?queryString="
As can be seen in the images named xss1.png and xss2.png (attached).
- relates to
-
CONFSERVER-43341 Inconsistent escaping returned by Confluence Search
-
- Closed
-
- links to