-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Medium
-
Affects Version/s: 5.0-OD-7, 5.0
-
Component/s: None
-
5
NOTE: This bug report is for Confluence Server. Using Confluence Cloud? See the corresponding bug report.
There is an arbitrary resource file download vulnerability triggered by a third party library org.tuckey.web.filters.urlrewrite.UrlRewriteFilter.
The urlrewrite.xml rules file shows the pattern that will trigger a <to type="forward"> forward rule, which is the equivelant of performing dp = request.getServletContext().getRequestDispatcher(resource); dp.forward(request, response);. This construct allows a user to forward requests to any resource file on the server, such as /WEB-INF/web.xml - which could potentially contain sensitive information like usernames and passwords.
web.xml
...
<!-- this filter is used to rewrite through the /s/* filter to add caching headers. see: urlrewrite.xml -->
<filter>
<filter-name>UrlRewriteFilter</filter-name>
<filter-class>org.tuckey.web.filters.urlrewrite.UrlRewriteFilter</filter-class>
</filter>
urlrewrite.xml
...
<rule>
<from>^/s/(.*)/_/([^\?]*).*</from>
<run class="com.atlassian.plugin.servlet.ResourceDownloadUtils" method="addPublicCachingHeaders" />
<to type="forward">/$2</to>
</rule>
</urlrewrite>
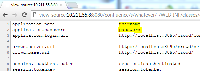
The attached screenshot shows this issue being exploited. It's recommended addPublicCachingHeaders be implemented without the vulnerable library until a patch is available.
- is related to
-
CONFSERVER-27693 Default application configuration files are available for download
-
- Closed
-
- relates to
-
CONFCLOUD-26888 Arbitrary resource file download in urlrewrite.xml
-
- Closed
-