-
Type:
Suggestion
-
Resolution: Unresolved
-
None
-
Component/s: Design, Projects - Permissions
-
49
-
34
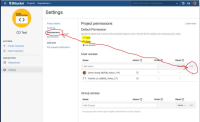
Problem Definition
It's easy for project Admins to make a mistake and not realize the implications of enabling the Project Default Permissions feature.
Suggested Solution
- A save button with a warning message
- A property that can disable the feature
Workaround
Develop a third party plugin that removes the feature.
- is duplicated by
-
BSERV-10091 Restrict permissions that can be granted by project or repository admins
- Gathering Interest
- relates to
-
BSERV-2675 Change default project permissions on all Projects
- Gathering Interest
-
BSERV-3554 Restrict granting of public access to global administrators
- Gathering Interest