-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Highest
-
Affects Version/s: 5.0 M5
-
Component/s: Agents
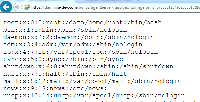
The ResolveURLServlet Servlet is vulnerable to an arbitrary file download attack. As the Servlet doesn’t implement its own authorization checks, this can be exploited anonymously.
By taking an attacker controlled url parameter and using this in a call to URLConnection.openConnection(), an attacker can supply the path of an arbitrary file location (e.g. file:///etc/passwd) to be served in the response. In testing, this vulnerability was used to retrieve private keys and login credentials of EC2 instances, ssh keys, configuration files, and most other data related to the on-demand service stack. The file system access appears to be restricted to that of the JVM process.
File: components\bamboo-web\src\main\java\com\atlassian\bamboo\agent\Classserver\ResolveURLServlet.java
public class ResolveURLServlet extends AgentServerServlet { private static final Logger log = Logger.getLogger(ResolveURLServlet.class); @Override protected void calculateResult(final HttpServletRequest httpServletRequest, final HttpServletResponse httpServletResponse) throws IOException, ClassNotFoundException { String url = httpServletRequest.getParameter("url"); log.debug("Resolving URL:" + url); final URLConnection urlConnection = new URL(URLDecoder.decode(url, "UTF-8")).openConnection(); final InputStream inputStream = urlConnection.getInputStream(); try { final byte[] content = IOUtils.toByteArray(inputStream); copyToResponse(httpServletResponse, content.length, APPLICATION_OCTET_STREAM, new ByteArrayInputStream(content)); } finally { inputStream.close(); } } }
The following screenshot demonstrates this vulnerability being exploited to download the /etc/passwd file from an on-demand instance.