-
Type:
Suggestion
-
Resolution: Unresolved
-
Component/s: IdP SSO - User Login
-
221
-
Problem
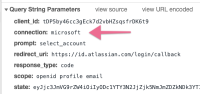
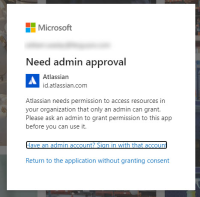
If you enforce SSO to your users through Azure, for example, and they use the social login "Continue with Microsoft", they will not log in with SAML, instead, they will use a specific flow.
As a result, a new app will be created at your Azure enterprise apps, called "Atlassian", and the user will be assigned to that app.
Suggestion
Integrate the social login functionality with the SAML implementation, so when the user clicks that button, the system automatically recognizes he is a SAML user.
Workaround
For now, users should use the email to trigger the SAML authentication flow
- is duplicated by
-
ID-7658 Allow org admin to enforce "Continue with Microsoft" social login option for user authentication
- Closed
- is related to
-
ID-6647 Allow customization on the login screen (enable or disable social login)
- Closed
- causes
-
BACCESS-16083 Loading...
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...