-
Type:
Bug
-
Resolution: Duplicate
-
Priority:
Low
-
Component/s: User Sync - SCIM Maintenance
-
None
-
Severity 3 - Minor
Issue Summary
It appears that SCIM synced accounts are able to modify some of their own SCIM syncable attributes such as job title, department, and organization.
Steps to Reproduce
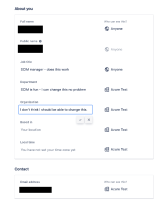
Below is a screenshot of what an organization admin sees for a SCIM synced account, note that full name, email address, job title, and department have the lock icon and cannot be changed. This is expected because when SCIM synced these changes should come from the identity provider (idP).
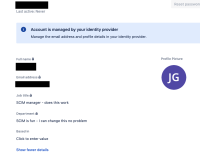
However, the user itself sees the following from https://id.atlassian.com/manage-profile/profile-and-visibility. The user is not able to change the full name or email address which is expected, but they are able to change job title, department, and organization which are attributes that are syncable via SCIM:
This is what is being SCIM synced from the idP (Azure in this case) for those three attributes:
"title": "SCIM manager" "urn:ietf:params:scim:schemas:extension:enterprise:2.0:User": { "organization": "SCIM Inc.", "department": "SCIM is fun" }
Expected Results
The SCIM synced attributes should be locked for the user just like they are locked for the org admin.
Actual Results
The SCIM synced attributes are modifiable for the user itself even though they are locked for the org admin.
Workaround
Since these fields are locked for the org admin, they have to ask the user itself to change them.
Syncing the user from the idP would work, but most idPs will not resync a user if the information in the SCIM directory has not changed. Because these users are making modifications to their Atlassian account and not the SCIM directory, the idP thinks nothing has changed and will not resync automatically. So the administrator would need to make a change to the user in the idP and then resync them to correct this.
- duplicates
-
ID-7396 Some fields are still editable at https://id.atlassian.com/manage-profile even with SCIM integration enabled
-
- Closed
-