-
Type:
Suggestion
-
Resolution: Timed out
-
Component/s: IdP SSO - Initial Setup
-
2
Issue Summary
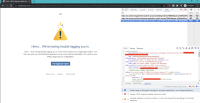
When an Identity Provider is sending a SAML Response without the Audience field inside <Conditions> element, we are throwing an error related to another field - the Destination URL:
"Hmm... we're having trouble logging you in. You'll need to talk to your organization admin - tell them we sent you, and that there appears to be an issue with the destination URL used for your SAML single sign-on configuration."
Steps to Reproduce
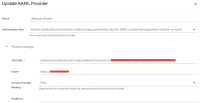
Make sure that the integrated IdP is missing the Audience configuration is missing, like the one below:
- Try to login into id.atlassian.com to see the failure
- Get a HAR file of the failed attempt
- Check the following error:
- error=access_denied &
- error_description=Audience is invalid. Configured: https://auth.atlassian.com/saml/1256cb51b-40b3-4d12-b984-5f9c4b383f4a
Request URL: https://id.atlassian.com/login/callback?application=jira&continue=https://abc.atlassian.net/login?redirectCount=1&application=jira&error=access_denied&error_description=Audience is invalid. Configured: https://auth.atlassian.com/saml/1256cb51b-40b3-4d12-b984-5f9c4b383f4a&state=eyJjc3JmVG9rZW4iOiIzNzcyZDhkZC1iYmJmLTRjOTQtODk5ZC0yNmY5ODg2ODg2YWMiLCJhbm9ueW1vdXNJZCI6ImUwOGI3NDM4LWZjNTEtNDk5ZS04MzFiLWY3ODc2NDdjOTY1NyIsInF1ZXJ5IjoiP2NvbnRpbnVlPWh0dHBzJTNBJTJGJTJGdW5peGZ5LmF0bGFzc2lhbi5uZXQlMkZsb2dpbiUzRnJlZGlyZWN0Q291bnQlM0QxJTI2YXBwbGljYXRpb24lM0RqaXJhJmFwcGxpY2F0aW9uPWppcmEifQ==
HTTP Version: http/2.0
Request method: GET
Full response: HTTP 403 Forbidden
Expected Results
The error message should state something like:
"Looks like your Audience configuration at your Identity Provider SAML configuration is either missing or misconfigured".
Actual Results
The following error message is returned:
"Hmm... we're having trouble logging you in. You'll need to talk to your organization admin - tell them we sent you, and that there appears to be an issue with the destination URL used for your SAML single sign-on configuration."
Failed <Condition> element: <saml:Conditions NotBefore="2021-12-31T00:00:49Z" NotOnOrAfter="2021-12-31T00:10:49Z"/> ------------------------------------------------------------------------------------------- Working sample - Microsoft: <Conditions NotBefore="2022-01-03T13:07:12.759Z" NotOnOrAfter="2022-01-03T14:12:12.759Z"> <AudienceRestriction> <Audience>https://auth.atlassian.com/saml/31b3dbbe-87dd-4dbf-b758-aeef158c72fa</Audience> </AudienceRestriction> </Conditions> ------------------------------------------------------------------------------------------- Working sample - Okta: <saml2:Conditions NotBefore="2022-01-03T13:44:54.277Z" NotOnOrAfter="2022-01-03T13:54:54.277Z" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"> <saml2:AudienceRestriction> <saml2:Audience>https://auth.atlassian.com/saml/31b3dbbe-87dd-4dbf-b758-aeef158c72fa</saml2:Audience> </saml2:AudienceRestriction> </saml2:Conditions>
Workaround
N/A