-
Bug
-
Resolution: Fixed
-
Low (View bug fix roadmap)
-
6.0, 6.3, 6.4, 7.1.0, 7.1.7, Archived Jira Cloud, 7.0.0
-
6
-
Severity 3 - Minor
-
NOTE: This bug report is for JIRA Server. Using JIRA Cloud? See the corresponding bug report.
Somewhat hard to exploit but still doable when it comes to cache poisoning. Steps to reproduce:
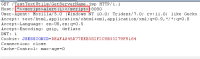
- Tamper with a GET request to http://<JIRA instance>/includes/decorators/global-translations.jsp with the Host header set to some XSS payload (e.g.
<script>alert(/xss/)</script>
- The offending lines in code pick this payload and browser renders it (observe an alert with text "xss")
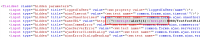
Offending code in /src/main/webapp/includes/decorators/global-translations.jsp#18:
17 <input type="hidden" title="ajaxUnauthorised" value="<ww:text name="'common.forms.ajax.unauthorised.alert'"/>"> 18 <input type="hidden" title="baseURL" value="<%=request.getScheme() + "://" +request.getServerName() + ':' + request.getServerPort() + request.getContextPath()%>"> 19 <input type="hidden" title="ajaxCommsError" value="<ww:text name="'common.forms.ajax.commserror'"/>">
- relates to
-
JRACLOUD-61888 XSS in /includes/decorators/global-translations.jsp
-
- Closed
-
- is cloned by
-
![[JIRA Server (Bulldog)] [JIRA Server (Bulldog)]](/images/icons/generic_link_16.png) JSB-86
You do not have permission to view this issue
JSB-86
You do not have permission to view this issue
- was cloned as
-
JDEV-37331 Loading...
[JRASERVER-61888] XSS in /includes/decorators/global-translations.jsp
| Minimum Version | New: 6 |
| Workflow | Original: JAC Bug Workflow v2 [ 2847092 ] | New: JAC Bug Workflow v3 [ 2930876 ] |
| Status | Original: Resolved [ 5 ] | New: Closed [ 6 ] |
| Symptom Severity | Original: Minor [ 14432 ] | New: Severity 3 - Minor [ 15832 ] |
| Workflow | Original: JIRA Bug Workflow w Kanban v7 - Restricted [ 2587921 ] | New: JAC Bug Workflow v2 [ 2847092 ] |
| Workflow | Original: JIRA Bug Workflow w Kanban v6 - Restricted [ 1580860 ] | New: JIRA Bug Workflow w Kanban v7 - Restricted [ 2587921 ] |
| Affects Version/s | New: Archived Cloud Version [ 77301 ] | |
| Affects Version/s | Original: 1000.174.0 Cloud [ 62594 ] |
| Description |
Original:
Somewhat hard to exploit but still doable when it comes to cache poisoning. Steps to reproduce:
* Tamper with a GET request to {{http://<JIRA instance>/includes/decorators/global-translations.jsp}} with the {{Host}} header set to some XSS payload (e.g. {code}<script>alert(/xss/)</script>{code} * The offending lines in code pick this payload and browser renders it (observe an alert with text "xss") Offending code in {{/src/main/webapp/includes/decorators/global-translations.jsp#18}}: {code:java} 17 <input type="hidden" title="ajaxUnauthorised" value="<ww:text name="'common.forms.ajax.unauthorised.alert'"/>"> 18 <input type="hidden" title="baseURL" value="<%=request.getScheme() + "://" +request.getServerName() + ':' + request.getServerPort() + request.getContextPath()%>"> 19 <input type="hidden" title="ajaxCommsError" value="<ww:text name="'common.forms.ajax.commserror'"/>"> {code} |
New:
{panel:bgColor=#e7f4fa} *NOTE:* This bug report is for *JIRA Server*. Using *JIRA Cloud*? [See the corresponding bug report|http://jira.atlassian.com/browse/JRACLOUD-61888]. {panel} Somewhat hard to exploit but still doable when it comes to cache poisoning. Steps to reproduce: * Tamper with a GET request to {{http://<JIRA instance>/includes/decorators/global-translations.jsp}} with the {{Host}} header set to some XSS payload (e.g. {code}<script>alert(/xss/)</script>{code} * The offending lines in code pick this payload and browser renders it (observe an alert with text "xss") Offending code in {{/src/main/webapp/includes/decorators/global-translations.jsp#18}}: {code:java} 17 <input type="hidden" title="ajaxUnauthorised" value="<ww:text name="'common.forms.ajax.unauthorised.alert'"/>"> 18 <input type="hidden" title="baseURL" value="<%=request.getScheme() + "://" +request.getServerName() + ':' + request.getServerPort() + request.getContextPath()%>"> 19 <input type="hidden" title="ajaxCommsError" value="<ww:text name="'common.forms.ajax.commserror'"/>"> {code} |
| Link |
New:
This issue relates to |
| Link | New: This issue relates to JRA-22946 [ JRA-22946 ] |
| Affects Version/s | New: 6.0 [ 29793 ] |