-
Bug
-
Resolution: Fixed
-
Medium (View bug fix roadmap)
-
None
-
5
-
NOTE: This bug report is for JIRA Server. Using JIRA Cloud? See the corresponding bug report.
I'm filing this in JRA because it looks like atlassian-gadgets is mainly maintained through JIRA project
If someone goes to plugins/servlet/gadgets/ifr with a broken url query parameter such as
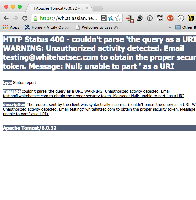
https://wh.atlassian.net/plugins/servlet/gadgets/ifr?container=atlassian&mid=1&country=US&lang=en&view=default&view-params={%22writable%22%3A%22false%22}&st=atlassian%3A99BsRDeg7EUdtS2P7WSYdXbvuyZl6RUJ71WH%2BhmLowxMr8BVSEdJdYLyVzO81%2FVi1ffVkF%2BUdW9D68zEvlbauTfgDMhjP0L0JCtW5RThr3AwvoXV0s8MUfVeLtNPN%2FbC5iBPuOUykXCKoYKZTXP9ayRCG1H3l5abZOrL7kCq7mHhlgyH0130%2FdVhDebkcxcQLlsOGrZ8mNsmGMoqkjO3Y2Lt98XWYduI1mfQT2AHCfd1ofIlP95cKzVXQD83khHDTB1U4ifDi2f8FhfsVjcna0V4%2FZu7JA%2Fqx%2FCtIP0%2F9eZqCNaaoJbMXvDRLiPhbXnES92TOq7Y4VKUPhp3wTEhjIlnTNQ%3D&up_isConfigured=true&up_isReallyConfigured=false&up_title=Activity+Stream&up_titleRequired=false&up_numofentries=10&up_refresh=false&up_maxProviderLabelCharacters=50&up_rules=&up_renderingContext=&up_keys=&up_itemKeys=&up_username=testing4%40whitehatsec.com&url=the%20query%20as%20a%20URI.%20WARNING:%20Unauthorized%20activity%20detected.%20Email%20testing@whitehatsec.com%20to%20obtain%20the%20proper%20security%20token.%20Message:%20Null;%20unable%20to%20part%20%20&libs=auth-refresh
Then the whole url value gets reflected in the error message. This can be used to produce rather ridiculous but still misleading pages, see the screenshot.
Perhaps validate url query parameter before trying to parse it.
This has been reported externally and we need to fix it.
- is related to
-
JRASERVER-43910 Content Spoofing in UpdateMyJiraHome
-
- Closed
-
- relates to
-
JRACLOUD-40793 "Content injection" issue in gadgets
-
- Closed
-