-
Suggestion
-
Resolution: Unresolved
-
None
-
0
-
Problem
With the project permission configured in the automation rule, project admin can still access to the System Admin user Authorization header information from the Send web request action:
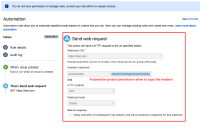
But I am a sys-admin and can not deposit one my personal token in a project automation where every project admin can read my token and use it for some obscure operations. This is affects the security of our Jira instance.
Suggestion
It would be great if the whole automation rule configuration field was disabled to access or copy from it.
Another option would be to hide the automation rules without being seen under Project Settings > Project automation > list.
- relates to
-
JSWCLOUD-22729 As an admin, I want to be able to hide values in automation rules, e.g. web requests using tokens in header
- Closed
- links to
| Form Name | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
[JIRAAUTOSERVER-522] Automation Rule project permission allow user to copy the Authorization header
| Labels | Original: iq-a4j | New: iq-a4j ril |
| Remote Link | New: This issue links to "Internal ticket (Web Link)" [ 979184 ] |
| Link | New: This issue relates to JSWCLOUD-26819 [ JSWCLOUD-26819 ] |
| UIS | New: 0 |
| Labels | New: iq-a4j |
| Link |
New:
This issue relates to |
| Description |
Original:
h3. Problem
With the [project permission configured in the automation rule|https://confluence.atlassian.com/automation074/permissions-for-project-automation-1141481144.html], project admin can still access to the System Admin user Authorization header information from the *Send web request* action: !image-2022-08-17-16-51-21-528.png|thumbnail! But I am a sys-admin and can not deposit one my personal token in a project automation where every project admin can read my token and use it for some obscure operations. This is affects the security of our Jira instance. h3. Suggestion It would be great if the whole automation rule configuration field was disabled to access or copy from it. Another option would be to hide all the automation rules without being seen under {*}Project Settings > Project automation > list{*}. |
New:
h3. Problem
With the [project permission configured in the automation rule|https://confluence.atlassian.com/automation074/permissions-for-project-automation-1141481144.html], project admin can still access to the System Admin user Authorization header information from the *Send web request* action: !image-2022-08-17-16-51-21-528.png|thumbnail! But I am a sys-admin and can not deposit one my personal token in a project automation where every project admin can read my token and use it for some obscure operations. This is affects the security of our Jira instance. h3. Suggestion It would be great if the whole automation rule configuration field was disabled to access or copy from it. Another option would be to hide the automation rules without being seen under {*}Project Settings > Project automation > list{*}. |
| Description |
Original:
h3. Problem
With the [project permission configured in the automation rule|https://confluence.atlassian.com/automation074/permissions-for-project-automation-1141481144.html], project admin can still access to the System Admin user Authorization header information from the *Send web request* action: !image-2022-08-17-16-51-21-528.png|thumbnail! Project admin users can copy or reuse the System Admin authorization header to do some issue operations which breach the security. h3. Suggestion It would be great if the whole automation rule configuration field was disabled to access or copy from it. Another option would be to hide all the automation rules without being seen under {*}Project Settings > Project automation > list{*}. |
New:
h3. Problem
With the [project permission configured in the automation rule|https://confluence.atlassian.com/automation074/permissions-for-project-automation-1141481144.html], project admin can still access to the System Admin user Authorization header information from the *Send web request* action: !image-2022-08-17-16-51-21-528.png|thumbnail! But I am a sys-admin and can not deposit one my personal token in a project automation where every project admin can read my token and use it for some obscure operations. This is affects the security of our Jira instance. h3. Suggestion It would be great if the whole automation rule configuration field was disabled to access or copy from it. Another option would be to hide all the automation rules without being seen under {*}Project Settings > Project automation > list{*}. |
In my opinion it is absurd that a solution to this is not yet available. I believe that almost all Security departments will no ifs and buts mouth the implementation of similar automations. Please consider the request quickly and carefully, this way the action related to HTTP requests is almost unusable!