-
Type:
Bug
-
Resolution: Fixed
-
Priority:
Highest
-
Affects Version/s: 8.2.0, 7.13.15, 7.19.7, 7.19.8, 8.1.3, 8.1.4, 8.5.6
-
Component/s: Core - Macros Platform
-
35
-
Severity 2 - Major
-
868
The behaviour described in this issue is as intended as we've restricted the velocity render modules that can be used by User Macros out of the box. Previously the modules that User Macros could access were entirely unrestricted, which presented a potential information disclosure risk. To address this risk, we introduced allow listing of modules for User Macros.
This change resulted in the issue detailed here. In response, we've improved the User Macro Administration interface to list modules that are used but have not been added to the allow list. Modules should be added to the sparingly to give the least required access possible. Administrators should carefully review what modules are added to ensure usage is in line with their expectations.
More information on the allow listing and modules available can be found at Confluence objects accessible from Velocity.
Again, we recommend against allow listing all velocity modules. As such I've removed the previously provided workaround that did just this.
The fix for this bug has been released to our Long Term Support release.
The fix for this bug is now available in the latest release of Confluence 7.13 and 7.19
Problem
Inserting a User Macro with variables in a Confluence page results in the variables to be displayed as it and not substituted with their values.
Environment
Confluence v7.19.7
Postgres 13
OS: Linux
Steps to Reproduce
- Login as admin
- Define a new User Macro with the below template code:
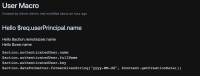
## @noparams #set($userDetailsManager = $containerContext.getComponent('userDetailsManager')) #set( $user = $action.remoteUser) <h1> Hello $req.userPrincipal.name</h1> <br /> Hello $action.remoteUser.name <br /> Hello $user.name <pre> $action.authenticatedUser.name $action.authenticatedUser.fullName $action.authenticatedUser.key $action.dateFormatter.formatGivenString("yyyy-MM-dd", $content.getCreationDate()) </pre>
- Set Macro Body Processing to Rendered
- Create a new page and add the macro created above.
- Save the page
Expected Results
(Add expected results for current action)
Variables in the macro are resolved.
Actual Results
(Add actual results for current action)
Macro displays as shown below:
Workaround
Please review the User Macro administration interface and the documentation at Confluence objects accessible from Velocity to determine what modules should be allow listed.
Modules can be added using the system property below
-Dmacro.required.velocity.context.keys=comma,seperated,key,values
- is related to
-
CONFSERVER-83283 Page Properties Report Macro does not render User Macros when any default context item value is null
-
- Closed
-
- relates to
-
CONFSERVER-83248 Page Properties Report Macro Does Not Render User Macros
-
- Closed
-
-
CONFSERVER-90583 Webwork velocity module cannot be used by user macros
-
- Gathering Impact
-
- was cloned as
-
CONFSERVER-97796 Variables in user macro are not resolved
-
- Closed
-
- mentioned in
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...
-
Page Loading...