Details
-
Bug
-
Resolution: Fixed
-
High
-
None
-
6.5
-
Description
NOTE: This bug report is for Confluence Server. Using Confluence Cloud? See the corresponding bug report.
Xss exploit found when using the existing Confluence Jira Macro.
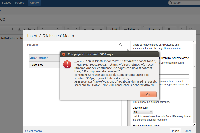
Occurs when adding this url to the Macro's dialog and selecting the 'refresh' icon on the dialog also appears when saving and viewing the page after the page has been saved with the exploit. (see screenshot)
To replicate:
Setup Jira Instance with attach dataset
On Confluence Instance setup an applinks with the Jira instance that has the dataset
Copy the JQL url by going into the search issues and listing all issues in the 'XSS' project and select 'Export' -> 'XML'
In Confluence Create a new Jira Issue Macro via the editor shortcut '{jira'
Paste the above url
Should get exploit upon selecting the refresh button on the dialog and also when saving the page
Attachments
Issue Links
- relates to
-
CONFCLOUD-29653 XSS vulnerability in Jira Macro *Existing*
-
- Closed
-
- mentioned in
-
Wiki Page Loading...