-
Suggestion
-
Resolution: Unresolved
-
None
-
6
-
At this moment, when a user that was previously logged via SSO has their session timed out in accordance with the Authentication Policy Idle session duration value, they are presented with the usual login pop-up:

Suggestion:
Implement a mechanism that would either:
- Automatically reuse the previous SAML attributes that were provided in the first SSO login, not requiring any extra steps from the end user.
- Keep stored, and allow the user to log in using the SAML attributes that were used in the first SSO login via a new button in the interface. For example, provide a new option to trigger the SSO authentication flow using the attributes that were already provided previously.
| Form Name | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
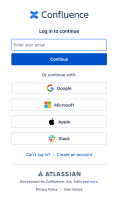
For my use case, we would like to have click-free seamless SSO, and thus the first option "Automatically reuse the previous SAML attributes that were provided in the first SSO login, not requiring any extra steps from the end user." is the closest fit of the 2. The second option requires the user to interact with another button on an already crowded dialog box so is not desirable for us.
Ideally, for a particular tenant, we would like the ability to set a tenant-wide (all auth policies) IDP setting that prevents the need for this sign-on IDP selection box in either the first or subsequent SSOs. The user is going to a particular tenant URL, that directs to a tenant-wide defined IDP URL, the user either signs in or their existing IDP sign on is used in a click-free way, then they are returned to the Jira tenant. Where possible, ID of the user is passed to the IDP so that in the case of multiple accounts it can select the correct ID/session to user without user action.